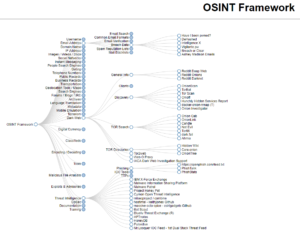
Open-source intelligence techniques and visualization
As Incident Response defenders, we will always be interested to know that how the attackers gain as much information about the target without ever touching the Organization and infrastructure or…
How to Start a successful threat Hunting for beginners?
What is Threat Hunting? Threat Hunting is a proactive approach to find the patterns of the existing malware in our network. As it’s a focused way to find the security…
The Rise of Artificial Intelligence in Cybersecurity
Definition of Artificial Intelligence (AI): Artificial Intelligence (AI) is a branch of computer science concerned with creating systems and algorithms that enable machines to perform tasks that would typically require…
Cybersecurity and 5G
5G (fifth-generation) technology promises to bring about significant improvements in speed, latency, and connectivity for IoT (Internet of Things) devices and other connected systems. However, 5G also presents new cybersecurity…
Cybersecurity for IoT devices
IoT (Internet of Things) devices refer to a wide range of physical devices and everyday objects that are connected to the internet and can collect and exchange data. Some common…
Existing Ransomware Attack on VMware EXSi Hypervisors
Ransomware attacks on VMware ESXi hypervisors are becoming increasingly common, as cyber criminals target the virtualization software used by organizations to run their IT infrastructures. In these attacks, the attackers…
Famous Data security breach of Payment Systems
As per the history, The Heartland Payment Systems data breach was a significant event in the history of cybersecurity, as it was one of the largest data breaches in history…
Multi factor authentication and its Vulnerabilities
Multi-factor authentication (MFA) is a security process that requires users to provide two or more forms of identification before gaining access to a service or system. The idea behind MFA…
Cybercrime and Cyber security
Cybercrime refers to criminal activities that are committed using the internet or other forms of digital communication. This includes a wide range of illegal activities such as hacking, identity theft,…
The Connection Between True and False in Cyber Security
False negative and True negative In the context of security, a false negative and a true negative refer to the results of a security system’s detection capabilities. A false negative,…